http://asert.arbornetworks.com/2009/06/a-deeper-look-at-the-iranian-firewall/
A Deeper Look at The Iranian Firewall
by Craig Labovitz In the previous blog post about the Iranian firewall, we explored macro level Iranian traffic engineering changes (showing that Iran cut all communication after the election and then slowly added back Internet connectivity over the course of several days). Like many other news reports and bloggers, we also speculated on Iran’s intent — how was the government manipulating Internet traffic and why?
Thanks to the cooperation of several ISPs in the region and Internet Observatory data, we can now do a bit better than speculate — we have pieced together a rough picture of what the Iranian government’s Internet firewall appears to be doing. The data shows that DCI, the Iranian state run telecommunications agency, has selectively blocked or rate-limited targeted Internet applications (either by payload inspection or ports).
I’ll step through several of these applications.
On average, Internet traffic is dominated by web pages (roughly 40-50% of all Internet traffic). And the vast majority of this web traffic (unless you happen to be Google or Facebook) goes into ISPs and the millions of associated end users (as opposed to traffic going out of a country or ISP). Iran is no exception.
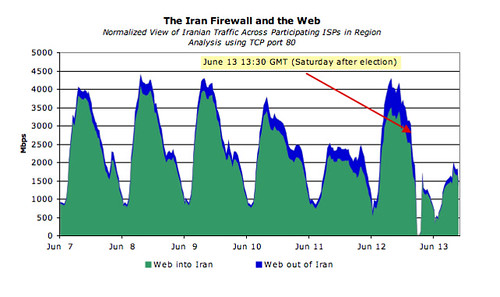
The below graph shows web traffic (TCP port 80) into Iran over the days before and immediately after the election. Though the graph clearly shows a brief post-election outage followed by a decrease in web traffic, the Iranian web traffic was comparatively unaffected by Iran filter changes. Based on reports of Iran’s pre-existing Internet filtering capabilities, I’d speculate DCI did not require significant additional web filtering infrastructure.
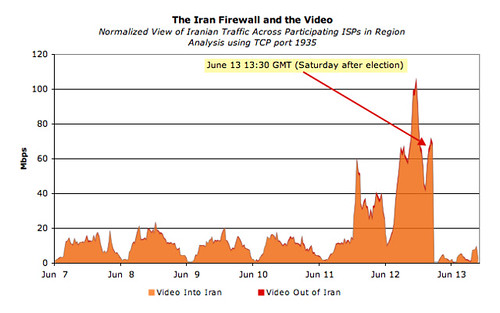
In contrast, the next graph shows streaming video traffic ([ame="http://en.wikipedia.org/wiki/Adobe_Flash"]Adobe Flash[/ame]) going into and out of Iran. Note the significant increase of video traffic immediately preceding the election (presumably reflecting high levels of Iranian interest in outside news sources). All video traffic immediately stops on the Saturday following the election (June 13th at 6:00pm Tehran / IRDT) and unlike the web, never returns to pre-election levels.
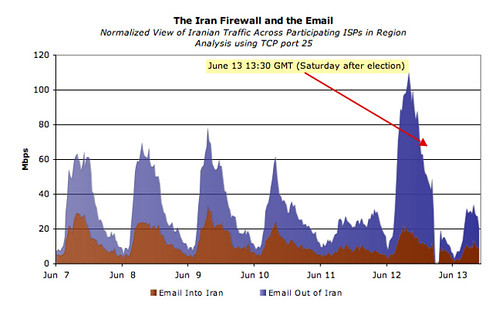
The next graph on Iranian applications filters shows email into and out of the country. Again note the run up in email traffic immediately preceding the election (especially outbound mails). And then? The data suggests DCI began blocking some outgoing email even before the election completed. Following the election, email returned at reduced levels (again, presumably because DCI had filtering infrastructure in place).
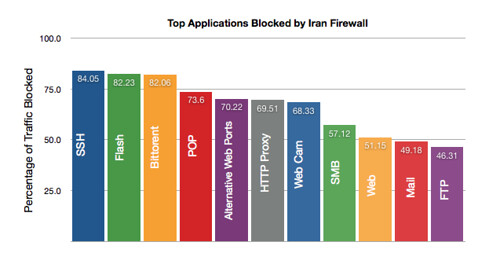
Finally, a look at the top applications now blocked by the DCI firewall(s). The chart shows average percentage decrease in application traffic in the days before and after the election. As discussed earlier, the Iranian firewalls appear to be selectively impacting application traffic. I’ll note that ssh (a secure communication protocol) tops the list followed by video streaming and file sharing.
While the rapidly evolving Iranian firewall has blocked web, video and most forms of interactive communication, not all Internet applications appear impacted. Interestingly, game protocols like xbox and World of Warcraft show little evidence of government manipulation.
Perhaps games provide a possible source of covert channels (e.g. “Bring your elves to the castle on the island of Azeroth and we’ll plan the next Ahmadinejad protest rally?”)
A Deeper Look at The Iranian Firewall
by Craig Labovitz In the previous blog post about the Iranian firewall, we explored macro level Iranian traffic engineering changes (showing that Iran cut all communication after the election and then slowly added back Internet connectivity over the course of several days). Like many other news reports and bloggers, we also speculated on Iran’s intent — how was the government manipulating Internet traffic and why?
Thanks to the cooperation of several ISPs in the region and Internet Observatory data, we can now do a bit better than speculate — we have pieced together a rough picture of what the Iranian government’s Internet firewall appears to be doing. The data shows that DCI, the Iranian state run telecommunications agency, has selectively blocked or rate-limited targeted Internet applications (either by payload inspection or ports).
I’ll step through several of these applications.
On average, Internet traffic is dominated by web pages (roughly 40-50% of all Internet traffic). And the vast majority of this web traffic (unless you happen to be Google or Facebook) goes into ISPs and the millions of associated end users (as opposed to traffic going out of a country or ISP). Iran is no exception.
The below graph shows web traffic (TCP port 80) into Iran over the days before and immediately after the election. Though the graph clearly shows a brief post-election outage followed by a decrease in web traffic, the Iranian web traffic was comparatively unaffected by Iran filter changes. Based on reports of Iran’s pre-existing Internet filtering capabilities, I’d speculate DCI did not require significant additional web filtering infrastructure.

In contrast, the next graph shows streaming video traffic ([ame="http://en.wikipedia.org/wiki/Adobe_Flash"]Adobe Flash[/ame]) going into and out of Iran. Note the significant increase of video traffic immediately preceding the election (presumably reflecting high levels of Iranian interest in outside news sources). All video traffic immediately stops on the Saturday following the election (June 13th at 6:00pm Tehran / IRDT) and unlike the web, never returns to pre-election levels.

The next graph on Iranian applications filters shows email into and out of the country. Again note the run up in email traffic immediately preceding the election (especially outbound mails). And then? The data suggests DCI began blocking some outgoing email even before the election completed. Following the election, email returned at reduced levels (again, presumably because DCI had filtering infrastructure in place).

Finally, a look at the top applications now blocked by the DCI firewall(s). The chart shows average percentage decrease in application traffic in the days before and after the election. As discussed earlier, the Iranian firewalls appear to be selectively impacting application traffic. I’ll note that ssh (a secure communication protocol) tops the list followed by video streaming and file sharing.

While the rapidly evolving Iranian firewall has blocked web, video and most forms of interactive communication, not all Internet applications appear impacted. Interestingly, game protocols like xbox and World of Warcraft show little evidence of government manipulation.
Perhaps games provide a possible source of covert channels (e.g. “Bring your elves to the castle on the island of Azeroth and we’ll plan the next Ahmadinejad protest rally?”)

